DS Record Lookup
Our DS Record Lookup tool helps you find the DS records for any domain. Use our tool to ensure that your DS records are correctly configured and that DNSSEC verification can be properly carried out.
DS Lookup
DS record lookup is a free lookup tool that retrieves the DS (Delegation Signer) records of a domain. This free tool can obtain the DS records of any domain from different DNS servers. Make DS record-checking a routine part of your DNSSEC maintenance. Regular monitoring helps you stay proactive in addressing any undue changes or potential security vulnerabilities.
How to Use the DS Record Lookup Tool?
Our DS Record Checker is designed to help verify the status of Delegation Signer (DS) records associated with your domain. You can use this free DS record checker by following these simple steps.
Input the Domain Name
In the domain name input field, enter the correct domain name for which you want to check the DS records. For the best results, we suggest you open the website whose domain records you want to check on a new tab and then copy the URL from the address bar. Then input that into the DS Record Lookup tool.
Choose a DNS Server
This tool lets you select a DNS server on which you want to check the DS records. Currently the options include:
-
Google
-
Cloudflare
-
Authoritative DNS
-
Quad9
-
Yandex
Get the DS Records
Hit the “DS Lookup” button to start the lookup process and wait a few seconds. Then, the DS records of the entered domain will show up.
About DS Record - What Is It?
The DS record plays an important role in the DNSSEC process. The DNSSEC process is used to verify the DNS responses that are provided to queries, such as the IP address of a domain, mail server information, etc. During the DNSSEC verification, a record known as DNSKEY is used to check the DNS query response to make sure it is not tampered with or altered in any way.
The DNSKEY record itself also has to be checked and validated during this process to ensure its integrity. That is where DS records come in. They contain a hash of the values contained in the DNSKEY records. DNS resolvers check the DS records and match the hash with the DNSKEY records. The hash value contained in the DS record is also known as the digest.
DS Record Example
For instance, we have a DS Record, e.g., example.com. IN DS 12345 8 2 ABCDEF123456789ABCDEF123456789ABCDEF123456789ABCDEF123456789ABCDEF
|
Domain |
Type |
Key Tag |
Algorithm |
Digest type |
Digest Value |
|
example.com |
DS |
123456 |
8 |
2 |
ABCDEF123456789ABCDEF123456789ABCDEF123456789ABCDEF123456789ABCDEF |
Let's break down the components of this DS record to help you understand how to intercept it:
-
"example.com.": This is the domain to which the DS record belongs. The trailing dot indicates the root of the domain.
-
"IN": Stands for Internet, indicating the class of the record.
-
"DS": The record type, specifically indicating a Delegation Signer record.
-
"12345": The key tag, a numeric value that identifies the DNSKEY record to which this DS record corresponds.
-
"8": The algorithm number used to create the digest. This case might represent the specified cryptographic algorithm used (e.g., RSA/SHA-256).
-
"2": The digest type, specifying the algorithm used to create the digest. In this example, it could represent SHA-256.
-
"ABCDEF123456789ABCDEF123456789ABCDEF123456789ABCDEF123456789ABCDEF": The digest, a cryptographic hash of the DNSKEY record associated with the child domain, ensures the integrity and authenticity of the child domain's DNS data.
Alternative Methods of Checking DS Records
Here are some other methods of checking DNS records. These methods vary a little bit depending on the OS of the system being used to do the lookup.
How to Check DS Records on Linux?
DS Records lookup on Linux involves using the dig command, Here's how to do it:
Open Terminal:
-
Press Ctrl + Alt + T to open the terminal in any Linux distribution.
-
You may also Press Alt + F2 to open the Run dialog and type gnome-terminal (for GNOME desktop), or konsole (for KDE desktop) and press Enter.
Use the dig Command:
-
Type the dig example.com DS command to check DS records.
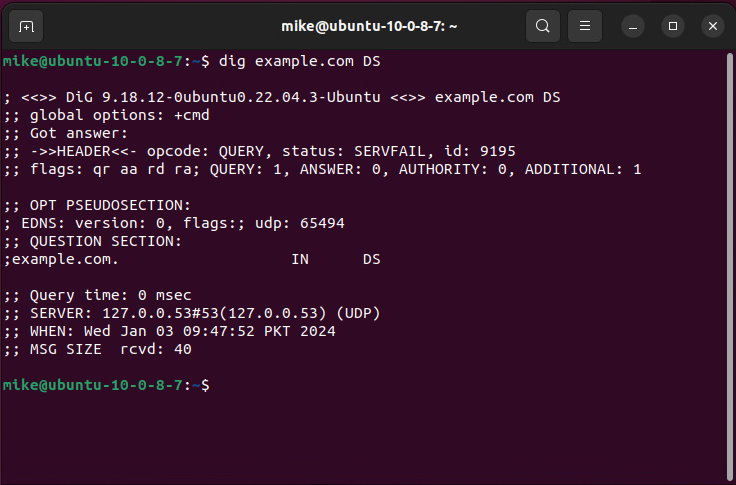
-
Replace "example.com" with the actual domain you want to investigate.
Review Results:
The DS records will be displaced, including the algorithm, key tag, digest type, and the digest itself.
How to Check DS Records on macOS?
MacOS users can also use the terminal and the dig command to check DS records.
Follow these steps:
Open Terminal:
-
Press Command + Space to open Spotlight Search.
-
Type "Terminal" and press Enter.
Use the dig Command:
Enter the dig example.com DS command, replacing "example.com" with the domain whose DS you’d like to examine.
Lookup DS Records:
The DS records for the specified domain will be presented, detailing the algorithm, key tag, digest type, and the actual digest values.
Why Check DS Records?
Here are some of the main reasons why you should regularly check DS records for your domain:
- Ensuring DNSSEC validation: Properly configured DS records are necessary for DNSSEC verification.
- Preventing DNS spoofing: DS records also help prevent DNS spoofing, a type of cyberattack in which a malicious party responds to DNS queries while posing as your domain.
- Preventing cache poisoning: Cache poisoning is also a malicious act that can occur without proper DNSSEC verification. Checking DS records helps prevent it.
- Preventing Man-in-the-Middle attacks: By checking DS records regularly, you can also prevent man-in-the-middle attacks.
Frequently Asked Questions
What information is included in a DS record?
A DS record consists of a key tag, algorithm number, digest type, and the digest. The digest is the hash of the DNSKEY record.
Are there any common issues or errors associated with DS records?
Yes. The most common issues include incorrect digest values, extremely long TTL, incorrect Key Tags, and so forth.. However, regularly monitoring and validating DNSSEC configurations can help identify and resolve such issues on time.
What happens if DS records are configured incorrectly?
Incorrectly configured DS records can lead to DNSSEC validation failures. DNSSEC-aware resolvers cannot establish the chain of trust, potentially resulting in DNS resolution issues for the domain. It can also lead to various types of security breaches.